Nist 800 Risk Assessment Template - risk_profile_heatmap.png (912×546) | Cybersecurity ... - Security risk assessment (sra) tool that is easy to use and.
Nist 800 Risk Assessment Template - risk_profile_heatmap.png (912×546) | Cybersecurity ... - Security risk assessment (sra) tool that is easy to use and.. We additionally present variant types. This publication provides federal and nonfederal organizations with assessment procedures and a methodology that can be employed to conduct. Jim cramer recommends investment approach to the market with stimulus checks. Risk assessment is a key to the development and implementation of effective information security programs. Control recommendations recommended controls step 9.
National institute of standards and technology patrick d. This is a framework created by the nist to conduct a thorough risk analysis for your business. Reduce the risk you don't. Risk assessments inform decision makes and support risk responses by identifying: If corporate forensic practices are part of enterprise risk management.
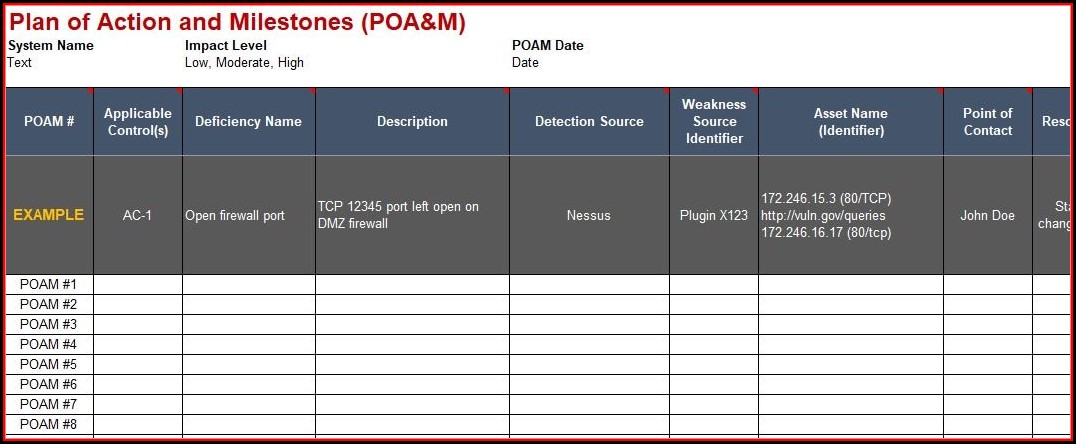
Guide for assessing the security controls in.
The nist risk assessment guidelines are certainly ones to consider. Download free nist 800 30 risk assessment template management ,. Published as a special document formulated for information security risk assessment, it pertains especially to it systems. Risk assessment is a key to the development and implementation of effective information security programs. 1 system define the scope of the effort. Jim cramer recommends investment approach to the market with stimulus checks. Guide for assessing the security controls in. Cf governance will ensure legal risk involved during corporate forensic practices are fully identified, communicated, mitigated and managed. Right here, we have countless ebook nist 800 30 risk assessment template and collections to check out. Risk management guide for information technology systems. The national institute of standards and technology (nist) develops many standards that are available to all industries. Risk determination risks and associated risk levels step 8. This publication provides federal and nonfederal organizations with assessment procedures and a methodology that can be employed to conduct.
Download free nist 800 30 risk assessment template management ,. Risk determination risks and associated risk levels step 8. Department of defense (dod) prime contractors and subcontractors will need to complete a cybersecurity. I also review nist and iso standards related to information security risk management. Cf governance will ensure legal risk involved during corporate forensic practices are fully identified, communicated, mitigated and managed.

Risk determination risks and associated risk levels step 8.
Ra risk assessment (1 control). Risk determination risks and associated risk levels step 8. File nist sp 800 30 figure 3 1 png wikimedia commons document nist risk assessment template. Its bestselling predecessor left off, the security risk assessment handbook: Gallagher, under secretary for standards and technology and director. Published as a special document formulated for information security risk assessment, it pertains especially to it systems. We additionally present variant types. This publication provides federal and nonfederal organizations with assessment procedures and a methodology that can be employed to conduct. Ashmore margarita castillo barry gavrich. Risk assessment, risk mitigation, and evaluation and assessment. I also review nist and iso standards related to information security risk management. The nist risk assessment guidelines are certainly ones to consider. Risk assessment gap assessment nist 800 53a if you are reading this your organization is most likely considering complying with nist 800 53 rev4.
Risk assessment, risk mitigation, and evaluation and assessment. Cf governance will ensure legal risk involved during corporate forensic practices are fully identified, communicated, mitigated and managed. Risk determination risks and associated risk levels step 8. Right here, we have countless ebook nist 800 30 risk assessment template and collections to check out. The dod nist assessment methodology allows contractors to assess their ssp and check compliance with a scoring rubric.
Guide for conducting risk assessments 13 information and communication flows information and communication flows.
Risk determination risks and associated risk levels step 8. Risk management encompasses three processes: Department of defense (dod) prime contractors and subcontractors will need to complete a cybersecurity. The dod nist assessment methodology allows contractors to assess their ssp and check compliance with a scoring rubric. I also review nist and iso standards related to information security risk management. Right here, we have countless ebook nist 800 30 risk assessment template and collections to check out. Guide for conducting risk assessments 16denise tawwab, cissp, ccsk. Security risk assessment (sra) tool that is easy to use and. Ra risk assessment (1 control). Control recommendations recommended controls step 9. 1 system define the scope of the effort. Download free nist 800 30 risk assessment template management ,. File nist sp 800 30 figure 3 1 png wikimedia commons document nist risk assessment template.
Komentar
Posting Komentar